
最新版 PA Server Monitor v9
最新版 PA File Sight v9

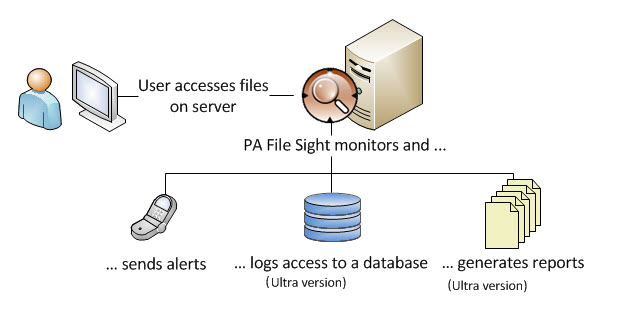
PA File Sight 是您在 Sarbanes-Oxley compliance 以及金融卡資料安全與 Payment Card Industry (PCI) compliance 中,協助您執行稽核的重要工具的一部分,甚至更多;PA File Sight 可以提供您伺服器在先前所無法獲得的檔案存取稽核紀錄。PA File Sight 提供詳盡的 Windows 檔案伺服器、稽核、報表及警示,它可以幫助管理者瞭解何人於何時對公司內部主機上之重要文件(包含檔案及目錄),在進行新增、修改、刪除、搬移或更改名稱!除此之外,您還能瞭解是使用哪一個程式作了這個動作!PA File Sight 也提供使用者檔案存取監控,並提供完整的檔案存取稽核記錄及報告。報表系統可以協助您瞭解過去發生了哪些事件。
Key Features:
- Ransomware Protection
- Data Loss Prevention - Prevent Information Leaks
- Audit File Access
- Trusted Applications (Application Whitelisting)
Ransomware Protection
- Detects ransomware attacks coming from the network and stops them
- Supports honeypots and heuristics
- Only allow executables to run that meet your rules
- Compromised computers are blocked from reaching files on other protected servers on the network.
Data Loss Prevention (DLP), Prevent Information Leaks
- Detects users copying files, and optionally blocks access
- Block access to cloud folders and external drives based on real-time rules
- Real-time alerts allow appropriate staff to investigate immediately
Audit File Access
- Audits who is deleting files, moving files or reading files
- Often used for compliance purposes
- The Ultra version will record this to a database for rich reports.
Trusted Applications
- Allow only trusted applications to run (Application Whitelisting)
- Protects against unknown applications (malware) from even starting up
- File I/O is allowed or denied in real-time based on your rules
- Real-time file and folder monitoring
- Reports username, IP address and computer
- Record creations, deletions, accesses, changes
- Alert on file and folder moves and renames
- Allow or prevent file access based on real-time rules
- Monitor file and folder permission changes
- Automatically block access for specific accounts
- Does not rely on Windows Native Auditing
Enterprise Robustness
- Optionally store audit data in Microsoft SQL Server (Ultra Edition)
- Robust security, your data stays on your servers - it is not sent to the cloud
- Monitor remote servers as easily as local servers
- Automatic failover with a hot standby server
- Access control to limit who sees what reports
- Backup SMTP server settings to help ensure alerts get out
File Access Auditing Compliance
Many compliance mandates require auditing file access and ensuring file integrity. PA File Sight can help meet those requirements, including those listed below:
- PCI (Payment Card Industry) DSS 10.5.5, 11.5, 12.9.5
- SOX (Sarbanes-Oxley) DS5.5
- GLBA 16 CFR Part 314.4(b) and (3)
- HIPAA 164.312(b)
- FISMA AC-19, CP-9, SI-1, SI-7
- ISO 27001/27002 12.3, 12.5.1, 12.5.3, 15.3
- NIST 800-53 and NIST 800-171
PA File Sight can monitor log files. It can alert on writes (changes) to files, but ignore the expected appends to log files. This lets you detect log tampering.
| Both Ultra and Lite can: | Ultra | Lite |
| Monitor: File activities (reads, writes, creates, deletes, moves, renames) | V | V |
| Alert: Real-time alerts via email, write to a log file, write to Event Log, play sound, call a URL, send Syslogs or SNMP Traps, etc. | V | V |
| Information: Accessed file, user account, user IP address*, file operation, date and time | V | V |
| * User IP address is available if the user is on Windows Vista or newer. Older versions of Windows did not support sending the IP address. | ||
| Only Ultra can: | Ultra | Lite |
| Database: Write file, user account, user IP address, file operation, date and time to an embedded SQLite or Microsoft SQL Server database. | V | |
| Reports: Generate reports over a period of time using the above database (Lite users would need to write to a text log file and then manually search the log file) | V | |
| Supports Endpoints: Supports File Sight Endpoints, including file copy detection, application whitelisting and preventing access to cloud drives and/or USB/external drives. | V | |
| Advanced Alerting: Alert on advanced usage patterns (like someone reading 15 files within 1 minute -- probably a file copy operation or a ransomware attack) | V | |
| Central Management: Manage multiple PA File Sight installations from a single central console | V | |
| Block External Drives: Has the Drive Sight monitor which can prevent external drives (USB, etc) from attaching to a server | V |
PA File Sight 已被設計為盡可能使用極少的系統資源。我們的目標是不影響正在運行的伺服器。
系統需求
System Requirements
Operating System:
» This application can be installed on a physical or VM platform that has one of the following operating systems installed.
» Windows Client: Windows 7, 8, 8.1, 10, 11
» Windows Server: 2008 SP2, 2008 R2, 2012, 2012 R2, 2016, 2019, 2022
» 64-bit Windows is required for the Central Server and Satellite software. The optional Endpoint can install on 32-bit or 64-bit Windows.
Software:
» .NET 4.6.2 or higher for report generation
Memory:
» 150 - 500 MB of free physical RAM for the monitoring process
» The amount of RAM needed will go up and down during the monitoring cycles. Every few minutes the monitoring service flushes unneeded memory to keep the process size small. RAM usage will increase when running certain data intensive reports. However, the increase will be temporary
Disk Space:
» 700 MB - 10 GB* of disk space
» The amount of required disk space varies widely based on the amount of data to store in the database. The program files are approximately 650 MB, and report files and logs are roughly 50 MB.
* The amount of I/O activity to be tracked and the length of time the data is kept has a large impact on database size.
CPU Usage:
» You configure the target CPU usage
» The Settings dialog lets you specify a target CPU Usage %. In general the monitoring service will attempt to keep CPU usage at or below that level. Occasionally, when flushing data to the database or when running large reports, the CPU Usage can spike higher, but that will be temporary and should not have an impact on the system.
Hardware:
The recommended hardware configurations for your version of Windows will be sufficient for PA File Sight.
Monitor Software Product Comparisons
In general the products are typically used for:
PA Server Monitor
Agentless server and application health and performance monitoringsoftware on local and remote servers and devices. Rich alerting and reporting.
PA Storage Monitor
In-depth analysis and tracking of file storage and directory sizes(local and remote), including file and file-owner information. Some monitoring capabilities as well as rich alerting and reporting.
PA File Sight
Real-time file access and auditing. Can report who accesses and deletes files. Ransomware protection, file-copy detection and USB drive blocking
High Level Comparison
| PA Server Monitor | PA Storage Monitor | PA File Sight | |
| Server Health | |||
| CPU usage, memory, NIC usage (performance counters), Event Logs, web pages, ping response, SNMP, services running, etc. | V | ||
| Free disk space checks. | V | V | |
| Predicted disk full date | V | V | |
| Server temperature or server room temperatures | V | ||
| File Auditing and Monitoring | |||
| Real-time file access auditing that can report who deletes or accesses files | V | ||
| Ransomware detection and protection | V | ||
| Information leak (file copy) detection and prevention (block users, block USB drives) | V | ||
| Polls files and directories for changes (local and remote systems, but no user activity reported) -- think host-based intrusion detection (IDS) | V | V | |
| Scans and records directory sizes for resource planning and reports | V | ||
| Scans and records file and file-owner information for detailed reporting and planning (ie who is storing MP3 files) | V | ||
| Additional Features | |||
| Alerts and reports | V | V | V |
| HTML tabular, graphical and CSV reports with optional email delivery | V | V | V |
| Server status report | V | V | V |
| Group summary report | V | V | |
| Runs as a service in the background | V | V | V |
Detailed Feature Comparison
Three of our products are very similar. To compare exactly how they are similar and different see the table below. All three products have the same list of response actions, so those are not shown.
| PA Server Monitor | PA Storage Monitor | PA File Sight | |
| Monitors | |||
| Action Scheduler Automate common IT tasks with the Action Scheduler. It will run your defined Actions when you specify. |
V | V | V |
| Active Directory Change Monitor Monitor creation, deletion, and changes of the Active Directory objects. |
V | ||
| Active Directory Login Monitor Monitor login and other security-related activity in Active Directory, Domain servers, and even for local logins. |
V | ||
| All-Systems-GO Reports to the All-Systems-GO service which can notify you if the monitoring installation is affected in any way that would prevent its from alerting. |
V | V | V |
| Bandwidth Monitor Monitor bandwidth, network error counts, broadcasts and other values from SNMP-based devices as well as from Windows Performance Counters. |
V | ||
| Calculated Status Monitor This monitor lets you calculate its status by running a script on the statuses of other monitors. |
V | V | |
| Citrix Presentation Server Monitor Monitor and alert on Citrix XenApp (Presentation Server) client connect and login response times. Alert if too slow, and record times for historical charts. |
V | ||
| Database Monitor The Database Monitor can watch that individual databases are up and running, keep an eye on the transaction log size, and alert if databases are added or deleted from a server. |
V | ||
| Directory Quota Monitor The Directory Quota Monitor keeps track of directory sizes, and executes actions if the directory sizes are over the quota. End users (directory owners) can be notified via email with the Monitor-Directed E-mail action. Includes reports. |
V | V | |
| Disk Space Monitor Monitor the free disk space on server drives. You can set the warning threshold in absolute size, or percentage of disk space. Includes reports and auto-configuration. |
V | V | |
| DNS Monitor Monitor the results of a DNS lookup, or a reverse DNS lookup. You can specify which DNS server the request should be sent to. If an unexpected result is returned, actions are fired. |
V | ||
| Drive Sight Protects servers and workstations by preventing CD/DVDs and/or external drives, including USB drives, from being attached. Any specified devices that are attached are immediately detached by the operating system so they cannot be accessed. |
V | ||
| Dynamic Server List Dynamic Server Lists are groups of serves that meet your criteria. Once the list is known, you can define Dynamic Groups based on the list, and use that group everywhere else groups are used. |
V | V | V |
| Email Monitor Monitor email messages in a POP3 or IMAP4 mail box for messages that contain specific text. When a match is found, alerts are fired. |
V | ||
| Environment Monitor Connects to an Esensors EM01b Websensor on the LAN and monitors the current temperature, humidity and luminescence, and notifies you if the values go above thresholds that you set. Historical reports as well. |
V | ||
| Event Log Monitor Checks any specified Windows Event Logs (Application, System, Security plus custom event logs) and executes actions you specify if a source you're interested in adds an event to the log. |
V | ||
| Event Validator Monitor Verifies that specific events, such as backup succeeded or anti-virus pattern file updated events are in the event log. If they are missing, fire alerts. |
V | ||
| Execute Scripts Execute your custom written scripts written in the Visual Basic Scripting Edition language. You can use custom or 3rd party ActiveX controls. The script determines whether to trigger actions using your own logic. |
V | V | |
| File Age Monitor Monitor file ages and alert if the files become too old (good for watching server queues, spool directories, etc). |
V | V | |
| File/Directory Size Monitor Track the size of a directory or a set of specific files within a directory. Includes reports. |
V | V | |
| File & Directory Monitor (CIFS Monitor) This monitor is a host-based IDS (Intrusion Detection System) that will notify you when the date, size or even content of a file changes on local files, or files on any CIFS share. File creation and deletion is also monitored. A good tool to help with configuration management as well. Auto-configuration functionality is available. |
V | V | |
|
File Sight Monitor The Ultra version also lets you: NOTE: This monitor can ONLY monitor drives on the local computer. Watching files on remote computers requires that the [PA Monitoring Product] service (or a Satellite) be installed on the remote computers. |
V | ||
|
File System Analyzer Directory Growth |
V | ||
| FTP Server Monitor The FTP Server monitor can login to FTP servers (including SSL-enabled FTP servers) to make sure they are up and running. |
V | ||
| Hardware Monitor Monitor the hardware status of ESX, Dell DRAC/iDRAC, HP iLO, IBM RAS and other IPMI-based devices. |
V | ||
| Inventory Alerter Alerts on inventory data collected by the Inventory Collector monitor. |
V | ||
| Inventory Collector Collects inventory information (hardware information, pending Windows Update, anti-virus status, etc) from a variety of sources including WMI, SNMP and an optional System Details application. |
V | V | V |
| Log File Monitor Periodically checks the content of one or more log files for target text. Target text and be a simple text phrase or a regular expression. |
V | ||
| Mail Server Monitor Monitor your mail servers (POP3, IMAP & SMTP) and validate that they are running and accepting incoming connections. |
V | ||
| Network Scan The Network Scan monitor will periodically perform a ping scan of a specified IP address range looking for new devices that are not already being monitored. They can automatically get added to the system and configured for monitoring. |
V | ||
| Performance Monitor The entire breadth of the system Performance Counters can be monitored allowing you to set actionable thresholds on CPU usage, memory usage, NIC traffic, etc. Performance counter values are stored in a database so you can view historical counter reports and understand trends. |
V | ||
| Ping Monitor Tests a connection/device by periodically testing it with a ping. No response or too great a delay triggers actions. Ping response times are recorded in a database for reporting and graphing. |
V | ||
| Plugin Monitor Runs an executable or external script launched via Windows, or via SSH, and parses the output to determine whether alerts should be fired. Plugins can also return values that are recorded to the database and can be charted. |
V | ||
| Process Monitor Monitor that specified processes are running on Windows or Linux servers. |
V | ||
| RD Gateway Monitor Remote Desktop Gateways and show currently connected sessions on a dashboard |
V | ||
| Server Temperature Monitor Using the free SpeedFan utility, the Server Temperature Monitor will watch the values from the various temperature probes on your server and notify you if they go above the thresholds you set. |
V | ||
| Service Monitor Watches system services and runs customized actions (including restarting the service) if they are not running. |
V | ||
| SNMP Monitor Connects to local or remote SNMP agents and queries SNMP object values. Custom MIBs are supported. The value is compared to a threshold that you set and actions are fired as specified. SNMP values are also recorded to a local database for reporting purposes. Supports SNMP v1, v2c and v3. |
V | ||
| SNMP Trap Monitor Receives SNMP Traps and optionally filters on trap text before running attached actions. |
V | ||
| Syslog Monitor Receives Syslog log events and optionally filters on incoming log text before running attached actions. |
V | ||
| Task Scheduler Monitors the enable/disable status and the Last Run Result value of Windows Task Scheduler tasks. |
V | ||
| TCP Port Monitor Makes a TCP connection on a specified port. Optionally send command text and check response text. Timing data is recorded for reporting purposes. |
V | ||
| User Quota Monitor Checks a data set produced by a File System Monitor scan for user disk usage. If they are over their quota, actions (including email sent to the end user) can be activated. |
V | ||
| Web Page Monitor Monitor one or many pages on a web site. Checks for positive cases (text that must be found), negative cases (alerts if error text found) and if the page has changed at all. Response times are checked and recorded, and reports can be generated to understand trends. |
V | ||
