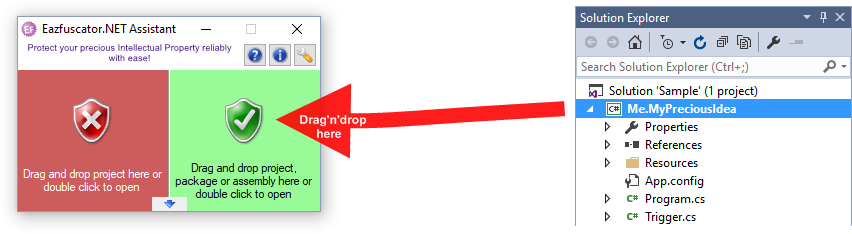
Eazfuscator.NET 是功能強大的.NET混淆工具。只需將文件放在綠色區域,將項目,程式包或程式集拖放到綠色位置,或雙擊以打開即可立即獲得保護。使用Eazfuscator.NET的最佳方法是將您的Visual Studio項目放在綠色區域中。應用保護後,每次在“發布”配置中構建項目時,程序集都會自動進行模糊處理。您還可以進行一些設置修改,可以使用完全配置.NET混淆屬性。軟體易於使用,並且具有多種受支持的混淆技術的自動代碼保護,支持自動優化和支持自動構建,以及可以混淆任何100%託管的.NET程式集,提供易於使用的GUI界面和經典命令行界面
Why is it good?
Eazfuscator.NET is easy as 1-2-3:
1. It protects your code, without breaking it — even in most complex cases — we have taken care of it. You can consider Eazfuscator.NET as a good partner who helps you a lot, and still doesn't bother you with any of his problems. If you have some really special protection requirements, pay attention to our code virtualization feature.
2. It really is easy to use: once protect your Visual Studio project with the Eazfuscator.NET Assistant tool, then forget about it. Every time you build your project in Release configuration, the assembly gets obfuscated automatically — you can release your code to the wilderness.
3. Need some settings to be changed? Are you sure? Then, do what you love: edit your code. Eazfuscator.NET is fully configurable by using .NET obfuscation attributes — in contrast to using alien-looking and unstable configuration files and UI wizards. All you need to know is in our complete product documentation.
更新介紹
- Preliminary .NET 9.0 support
- Code virtualization now supports interpolated strings
- Improved ASP.NET Core support
- Improved JSON serialization support
- Improved Entity Framework Core support
- Improved performance of method flattening
- Improved documentation
- Fixed issue that could lead to a loss of enum type information when used in interpolated string expression
- Fixed issue that could leave XAML property reference with invalid namespace token after obfuscation
- Fixed issue with nullable types when using code virtualization
- Fixed issue that could cause type loading error when interface method was implemented in one of the base classes
- Fixed issue that could lead to assembly loading error during obfuscation with code virtualization enabled
- Fixed issue that could lead to assembly loading error during obfuscation of .NET Framework 4.x assemblies
- Fixed performance regression of method inlining that occurred during obfuscation
Symbols renaming
When we develop a program, we often present the most valuable information in form of symbol names: names of functions, variables, classes. This information is precious to an intruder who wants to get an understanding of our software.
The simplest and the most effective approach to conceal this information is to make the names irrelevant to what happens inside the program. We will just make the names of all the symbols unreadable — when it is possible.
String encryption and compression
Other thing that discloses the information about how a program functions is strings. To hide this information, Eazfuscator.NET substitutes the strings in your code with calls of special encryption functions, which render your strings perfectly at runtime, leaving them unreadable to an intruder. Also, these functions make the size of your strings lesser by compressing them.
Code and data virtualization
There are situations when we want to protect a part of our program more than anything else. We think of a person who would inspect our code as of well-motivated and of one who would go for a desperate measures. In this case, the symbols and strings protection is just not enough.
Here we offer you a radical approach: to change the way your program is presented in memory and on disk. Our code virtualization technique translates your .NET byte code to a totally unrecognizable random-generated byte sequence, which still perfectly functions at runtime. In other words, each time you obfuscate your program, we generate a new custom virtual machine to work for you!
Automatic code optimization
Many of us have dreamt of being able to know every performance-sensitive aspect of the platforms and programming languages we use. This way, we would always be careful to write only the fastest code. Still, not many of us are actually aware of all the performance-related details, which often change while the platform evolves.
With Eazfuscator.NET, you don't need to be a .NET performance expert to make the top-performing applications. We perform code optimization automatically for you by replacing code fragments which are proven to be slow with their faster equivalents — behind the scenes. In some cases, optimization may make your code faster by hundreds of times. Right now there is a big list of scenarios we take into account during the optimization. And this list will grow.
Resource encryption and compression
If your product is ambitious enough, it includes many valuable assets. Almost any popular application includes a designer-created icon set. If you are a game developer, the original game sounds would cost you a lot. When your assembly resources contain security information such as private keys, it becomes very sensitive.
To cover all these things protected, we transparently encrypt the resources for you when you ask it.
Code control flow obfuscation
The .NET languages compilers usually generate similar MSIL code fragments for the similar fragments of your high-level code. This fact allows the decompiler tools to reverse-engineer the high-level code (in C#, for example) from the .NET assemblies.
Eazfuscator.NET supports an advanced technique called control flow obfuscation, when the MSIL code gets replaced with functionally equivalent, but different instructions. Decompilers often crash on such code, so this may stop an intruder from trying to break into your assembly.
Assemblies merging and embedding
In some cases, we need to make one assembly from several ones. There are two methods of doing this: merging and embedding.
Eazfuscator.NET merges or embeds assemblies for you in easy way: you need to add one line of code to your project, where you specify which assembly to mix in. We are responsible for all this to be done correctly and quietly — during the obfuscation process.
XML documentation filter
If you are developing a class library, it is very probable that you use the auto-generated XML documentation files. The security problem concerning them is that they contain information describing your library implementation details: names and descriptions for private types, methods and fields.
We take care to automatically remove all the implementation-disclosing data from the XML documentation files.
Debugging support
After your assembly is obfuscated with Eazfuscator.NET, it doesn't become a brick of non-debuggable mess. You can always get a line number where an unhandled exception appeared, view a readable stack trace, and even attach the debugger to walk through your obfuscated code.
Supported platforms and technologies
- .NET 5.0 – 8.0
- .NET Standard versions 1.0 – 2.1
- .NET Core versions 1.0 – 3.1
- .NET Framework .NET Framework versions 2.0 – 4.8.1
- XAML with intelligent renaming of symbols
- Enterprise-grade technologies: ClickOnce, VSTO, and many others
- Universal Windows Platform (UWP)
- Gaming technologies: Unity, MonoGame, XNA
- Third-party platforms: Mono and Xamarin
- Integration with Microsoft Visual Studio Microsoft Visual Studio 2005–2022
- Integration with JetBrains Rider JetBrains Rider 2019.1+
- More…
The last but not least. The User Interface
Eazfuscator.NET provides an easy to use GUI interface as well as classical command line interface.
| Single Developer License | Site License | |
| Core Features | V | V |
| Deterministic Obfuscation | - | V |
| Concurrency Level | 16 | ∞ |
| Number of Developers | 1 | ∞ |
| Support | V 48/5 P2 Support is provided with a guaranteed 48h response time during business days (Monday to Friday) with a normal priority in the support queue |
V 24/5 P1 Support is provided with a guaranteed 24h response time during business days (Monday to Friday) with the highest priority in the support queue |
Core Features
All core features Eazfuscator.NET has to offer
Deterministic Obfuscation
Deterministic obfuscation allows to produce an assembly whose byte-for-byte output is identical across obfuscations for identical inputs.
By default, obfuscator output from a given set of inputs is unique, since the obfuscator uses randomly generated cryptographic material for every obfuscation. You can use deterministic obfuscation feature to produce a deterministic assembly, one whose binary content is identical across obfuscations as long as the input remains the same.
The feature is only available in Site License edition.
Concurrency Level
The Single Developer License allows to simultaneously utilize up to 16 CPU cores (16C/32T) of a computer for Eazfuscator.NET.
The Site License does not impose limitations on concurrency.
Number of Developers
Single Developer License allows only one developer to use Eazfuscator.NET.
The Site License allows an unlimited number of developers to use the product as long as they belong to one company.
System Requirements
- Windows 8.1+
- .NET Framework 4.7.2+
Cloud Combine
Cloud Combine is easy to use IDE for Cloud Services.
特色
Supported cloud platforms and services
- Amazon AWS: S3
- Google Cloud: Cloud Storage
- Microsoft Azure: Storage (Blobs, Tables and Queues)
- File Transfer Protocol: FTP, FTPS and SFTP
Browse cloud storage
Cloud Combine allows you to browse your cloud storage in a way similiar to Windows Explorer. You don't have to think about the internals of Azure blob storage or Amazon S3 — you just do your regular file operations, we take care of the rest.
Download and upload
You can use Cloud Combine to download and upload data of any type and size. Just drag your files or folders where you want them to be. All the data transfers are fail-safe: we will continue trying until your data is in place.
Transfer data within a storage or between different accounts/clouds
If you want to quickly move, copy or duplicate blobs inside your cloud storage, or migrate data between two different accounts or clouds, Cloud Combine handles this for you absolutely transparently — just the way you copy your files and folders on local computer.
Share your storage data
You can always make a public web link to your files, containers/buckets or directories with Cloud Combine, as well as to make some of your entire containers/buckets public. See screenshot
Manage your storage settings
With Cloud Combine, you can manage your cloud storage settings (for example, S3 Storage Class or Server Side Encryption) easily.
Amazon S3 versioning
Cloud Combine provides simple and intuitive support for Amazon S3 versioning. It just works when you need it.
Automatic parallelization
Cloud Combine will execute several cloud operations in parallel to gain a significant speed-up when appropriate.
Single-panel mode
Most of us are familiar with the standard file management tool: Windows Explorer. By default, Cloud Combine offers you the user interface similar to this standard. You just browse your cloud storage as if you were exploring your local drives and folders. If you want to download or upload file or folder, just drag it to/from a Windows Explorer window, copy/paste, or use Upload/Download toolbar buttons.
Double-panel mode
Many power users have their favorite file manager applications: Total Commander, FAR Manager, Midnight Commander etc. All these applications use the principle of working with files in two panels, allowing the user to operate more quickly using only keyboard. We have brought the productivity of this approach to Cloud Combine by adding the double-panel mode. In this mode, you work with your on-cloud and local data side-by-side, and all the traditional keyboard shortcuts are supported. You can always easily switch between single and double panel modes.
系統需求
Windows Vista SP2 or newer


