CopyRight Standard 可以讓您輕鬆的遷移網絡共享文件、檔案、資料夾、NTFS權限、共享權限、群組和用戶帳戶(甚至密碼)等等,從原始電腦到目標電腦。這是個全方位的解決方案,可以支援您從規劃階段到實際遷移的階段。
CopyRight Standard使用直觀的用戶介面,讓您可以輕鬆的點幾下滑鼠就創建複本,您可以簡單地選擇原始文件以及目標資料夾,或是增加電腦或Active Directory掃描任務,以收集即時的資料用來進行遷移規畫,您也可以選擇需要的儲存格式(如Text文字檔、Microsoft Access檔案或Microsoft SQL Server檔案)。其所創建的任何作業,可以在選定的日期、時間或區間自動運行。此外其用戶介面可以整合Windows® Explorer,並提供一個與內建的Xcopy command非常相似的命令行界面。
Below you can find a list of CopyRight2's unique and innovative file server, NAS, Microsoft Internet Server, Active Directory and Azure migration related key features.
- Copies network shares, files, folders and accounts including their security information (Discretionary Access Control List, System Access Control List, Owner and Group). Optionally the permissions of the destination can be inherited.
- Synchronizes source and destination, copying only files that have changed since the last synchronization run. Optionally deletes files that no longer exist at the source (as known as "lonely files").
- Graphical user interface to run jobs interactively or to schedule them for later execution time.
- Real time synchronization to eliminate user down time during cut-over.
- Comparison report for migrated data and NTFS permissions.
- Support for Windows® cluster services.
- Support for server consolidation scenarios resulting in a lower TCO.
- Rollout planning module for large scale migrations, allowing you to plan and execute the project from a central location.
- Migration of local and server based Windows® user profiles.
- Automatic translation of Windows® shortcuts (.LNK) files.
- Automatic update of most recently used file references in user profiles.
- Automatic update of persistent network connections stored in user profiles.
- Migration of Windows® reparse points (directory junctions and symbolic links).
- Migration of Windows® NTFS hard links.
- Migration of IIS/FTP site configurations from IIS 6.0 (Windows 2003) and newer to IIS 7.5 (Windows 2008 R2) and newer.
- Possibility to use the GUI to connect to a remote server that has CopyRight2 installed to operate the software from a centralized location such as a notebook.
- Besides of automatically copying user and group accounts contained in file or share permissions as needed, CopyRight2 has the possibility to selectively copy and synchronize user and groups accounts without copying file data or shares.
- Optionally copies and / or synchronizes user account passwords.
- Optionally allows the definition of time frames, causing the migration to stop when the maintenance window ends.
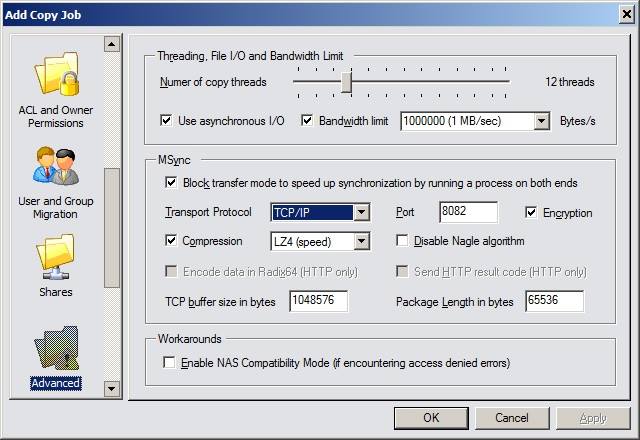
- Allows the definition of a maximum bandwidth in KB/s to limit the amount of bandwidth consumed by copy jobs.
- Supports DFS (Distributed File System) either clustered or non-clustered to migrate file shares while preserving the existing UNC namespace and automatically updating the corresponding DFS mapping.
- Integrated into Windows® Explorer.
- Additionally offers a command line interface (CLI) to provide a script based interface to existing processes or applications.
- Multi-threaded copy engine maximizing throughput by automatically optimizing itself depending on file characteristics.
- Continues where Microsoft Robocopy stops.
- Compresses or decompresses files while copying according to user settings.
- Migration of NTFS encrypted files preserving the encryption.
- Migration of client side caching settings (CSC) of network shares.
- Copies or changes the creation date of files and folders.
- Copies short file names to preserve 16-bit application compatibility.
- Can automatically compress old or rarely used files while copying.
- Filtering to exclude files from getting copied, depending on their creation time, change time or the last access time.
- Copies users, local groups, local group members, global groups and global group members.
- By default preserves user and group names during migrations.
- Optionally allows the definition of prefixes and suffixes for users, local groups, global groups and file shares to circumvent naming conflicts during server consolidations.
- Features a graphical user interface to optionally create a mapping table defining which users and groups in the source environment relate to which users and groups in the destination environment.
- Supports all possible migration scenarios in the same or between different domains (domain member to domain member, domain controller to domain controller, domain member to domain controller, domain controller to domain member).
- Modifications to file security or file attributes can be applied without actually moving any data to ReACL file permissions (replace), AddACL (add) or DeACL (remove/cleanup) specific accounts from permissions.
- Supports migrations utilizing the Windows® sidHistory feature.
- Supports non domain computers running in workgroup mode as source or destination as well.
- Copies Apple Macintosh resource forks.
- Even files that are "normally" not accessible can be copied in the same way it is done by Windows® backup features, allowing you to backup all your files, even those where the access control list (ACL) would deny access.
- Supports the Windows® shadow copy feature to copy files that are locked and in use.
- Creates an error log file.
- Optionally creates an entry within the Windows® event log on success or failure.
- Optionally sends a result email in case of success or failure including the log file as attachment.
- Offline migrations of files, file shares, groups and users (including passwords) allowing the migration of servers between disjoint networks.
- Import of Samba PDBEdit exports to import user account passwords from Linux.
- Migration of Active Directory user accounts, contacts, security groups and distribution lists (local, global, universal).
- Migration of Active Directory OUs and container structures.
- Migration of Active Directory object’s permissions or possibility to inherit permissions from the destination OU/container.
- Object class specific definition of Active Directory attributes to migrate (include / exclude / all class attributes).
- ActiveScript support to transform user, group and contact attributes (called for each object migrated) during migration from source to destination.
- Possibility to define scripts executing at the beginning and/or the completion of executed copy jobs.
- Exclude specific user or group accounts from the migration.
- Specify Active Directory accounts to migrate by using an LDAP query filter.
- Migration of data including file shares, share level and NTFS permissions to Azure storage accounts.
與其他類似產品比較表
| Feature | RoboCopy | Competitors | CopyRight2 |
| Block transfer mode not relying on Microsoft's SMB protocol (similar to RSync) to speed up copying and synchronizations across low bandwidth, high latency connections, reusing already existing data at the destination up to the byte level. | V | ||
| Compression & encryption (if using block transfer mode) of the transmitted data. | V | ||
| SHA-256 hash validation to ensure each file was successfully transferred. | V | ||
| Guaranteed bandwidth limit specified in kilo, mega or gigabit per second (packet delay in milliseconds is not a guaranteed bandwidth limit!). | V | ||
| Copies file security inner domain (AGDLP RBAC, without server local users or server local groups involved). | V | V | V |
| Copies permissions inner domain (AGLP RBAC, including local users and local groups on member servers requiring migration of those users and groups to the target member server or the domain). | V | V | |
| Copies permissions from/to workgroup mode configured systems (including local users and local groups). | V | V | |
| Copies permissions cross domain (including local users, local groups, global users and global groups). | V | ||
| Copies network shares during file copy. | V | V | |
| Preserves user passwords during migration. | V | ||
| Copies very long file names. | ? | V | |
| Preserves folder and file timestamps during file migration. | ? | V | |
| Copies compressed files and folders. | ? | V | |
| Copies encrypted files and folders. | ? | V | |
| Copies Apple Macintosh resource forks. | V | ||
| Preserves short file names for 16-bit application compatibility. | ? | V | |
| Includes an InfraStructure Reporting feature constituting a full fledged solution beginning at the early planning stages by delivering data about the source environment in a user friendly way at no additional costs and integrated into one solution framework. | V | ||
| Can notify an operator of job completion by email. | ? | V | |
| Native 64-Bit version available. | V | V | |
| Has a graphical user interface to interactively manage copy jobs. | V | V | |
| User interface can connect to remote server having solution installed on. | V | ||
| Supports Windows cluster services and NAS clusters. | V | ||
| Template based rollout planning module for large scale migration projects. | V | ||
| Real-time synchronization between source and target in order to limit the time frame required for the migration to a minimum. | V | ||
| Pause and resume the copy operation where it left off without having to "walk" the directory tree again while copying/updating/deleting any data to the target that was changed while it was stopped. | V | ||
| Support for server consolidations to lower TCO. | V | ||
| Comparison report for data including NTFS permissions. | ? | V | |
| No inventorying required but possible (for reporting) | ? | ? | V |
COPYRIGHT2
MID-RANGE EDITION
- Includes 5 support incidents
- Up to 50 Server/NAS activations for data, Active Directory and IIS migrations per year
- Up to 1,000 Computer and Profile Migrations
- Includes all Add-Ons:
- Password Migration
- IIS Migration
- Azure Storage Account Migration
- DFSR Migration
- Two years of warranty
COPYRIGHT2
STANDARD EDITION
- Unlimited 24/7 support
- (Telephone, Email, Chat)
- Two Server/NAS activations for data, Active Directory and IIS migrations (Source & Target)
- Up to 150 Computer and Profile Migrations
- Includes all Add-Ons:
- Password Migration
- IIS Migration
- Azure Storage Account Migration
- DFSR Migration
- Two years of warranty
COPYRIGHT2
ENTERPRISE EDITION
- Includes 10 support incidents
- Unlimited Server/NAS activations for data, Active Directory and IIS migrations
- Up to 5,000 Computer and Profile Migrations
- Includes all Add-Ons:
- Password Migration
- IIS Migration
- Azure Storage Account Migration
- DFSR Migration
- Two years of warranty
Requirements
CopyRight2 has the following hardware requirements:
- At least 4GB of RAM
- At least 1 CPU with 2 cores (or hyper-threading)
- At least 256MB of available disk space
CopyRight2 supports the following versions of Windows:
- Microsoft Windows® NT 3.51
- Microsoft Windows® NT 4.0
- Microsoft Windows® 2000
- Microsoft Windows® 2003 / Windows® 2003 R2
- Microsoft Windows® 2008 / Windows® 2008 R2
- Microsoft Windows® 2012 / Windows® 2012 R2
- Microsoft Windows® 2016
- Microsoft Windows® 2019
- Microsoft Windows® 2022
- Microsoft Windows® XP
- Microsoft Windows® Vista
- Microsoft Windows® 7
- Microsoft Windows® 8.0 / 8.1
- Microsoft Windows® 10
- Microsoft Windows® 11
- Windows® Cluster Services
CopyRight2 supports the following Network Attached Storage Solutions:
- Netapp® ONTAP7 & ONTAP8 (7mode or clustered), ONTAP9
- EMC® Celerra, VNX and Isilon
- Hitachi® HDI & HNAS
- Synology
- NetGear ReadyNAS
- Nutanix
- Many others...
CopyRight2’s IIS FTP/HTTP Site Migration Add-On supports the following IIS versions:
- IIS 5.0 (only as source)
- IIS 6.0 (only as source)
- IIS 7.0 (only as source)
- IIS 7.5
- IIS 8.0
- IIS 8.5
- IIS 10 Build 1607 and newer (1709, 1809, …)
BufferShield
Over the past few years, there has been a sharp rise in the number of reported vulnerabilities and worms.
The main reason existing security technologies fail to protect organizations from emerging security threats, is that they rely on incomplete or inaccurate information. Some rely on analyzing network traffic, others use signatures of known attacks, whilst some combine both.
But, none of these technologies can effectively protect organizations from the new breeds of computer worms and other malicious attacks.
Our customers use BufferShield in a wide variety of ways:
- Add an additional security layer to Windows update, virus scanners and firewalls
- Enhance the security on current desktop and server operating systems
- Enhance the security on critical infrastructure systems
- Enhance the security for no longer supported legacy OS like Windows NT 4.0 and Windows 2000, still being targetted
- Survive the day-0 phase, that any publically known vulnerability goes through, until hotfixes / patches are available
- As a honeypot component, triggering an alarm in order to discover new and harmful threats at the earliest possible stage
Scription
The product Scription allows the administrator to customize the user's environments during log-on, adapted to their authorizations and requirements. This was so far only possible with the help of different tools and batch files ("conventional" logon scripts). A substantial maintenance expenditure and the maintenance of the various tools usually lead to increased personnel resources requirement, resulting in increased TCO's.
The configuration is managed by using a graphical user interface.
- Already implemented at customer sites with small, medium and large sized networks, ranging from 10 up to 60.000+ users (including banks, postal services companies, ...)
- Comprehensive online help
- Structured approach
- List of possible configuration changes
- Different conditions combinable using logical operator
- Configurable intervals for configurations
- Active Logon Scripting
- Only necessary elements will be delivered to the client
- Support for all Microsoft Windows® 32-Bit Operating Systems
- Windows®-NT 3.51 Workstation / Server
- Windows®-NT 4.0Workstation / Server
- Windows®-NT 4.0 Terminal Server
- Windows® 2000 Professional
- Windows® 2000 Server / Advanced Server
- Windows® XP
- Windows® 2003 Server
- Windows® 95
- Windows® 98
- Windows® ME
- Windows®-NT integrated security !
- Active Directory Support
- Easy installation procedure (Microsoft SMS deployable)
- Flexible and extensible
- ODBC-database support
- Microsft AccessODBC Driver
- Microsoft SQL-Server 6.0 - 2000
- Replication mechanism
- Changes can be explicitly replicated to domain controllers
- Add additional information to the Microsoft S.M.S. inventory
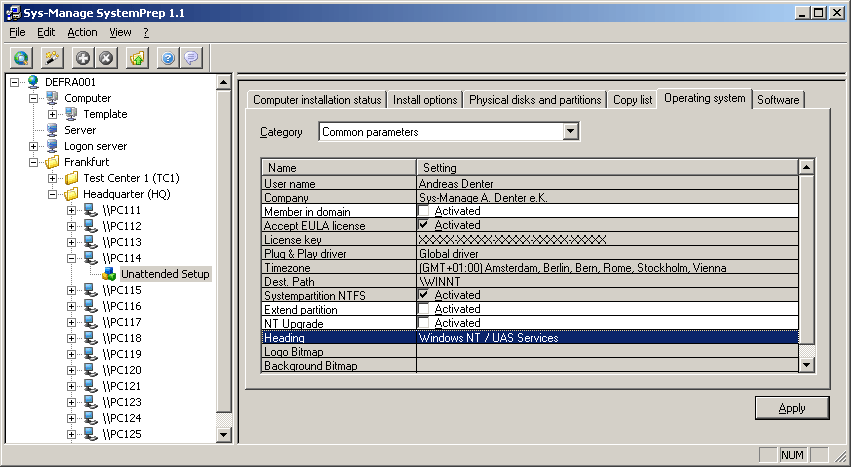
SystemPrep
SystemPrep is a product for the automated, rapid and safe deployment of operating systems, additional software and drivers onto remote computers. It supports single site as well as multiple site WAN scenarios, with minimal configuration effort.
SystemPrep complies to the Intel Wired for Management (WfM), Preboot Execution Environment (PXE) 2.x specifications.
To bootstrap clients into the installation process it supports:
- PXE & TCP/IP Boot ROMs
- PXE & TCP/IP Boot ROM code located on a 3,5” disk
- conventional DOS based installation disks
To automatically power on a previously shutdown computer, before the installation takes place, it optionally supports Wake On LAN technology.